Table of Content
The Internet & technology has completely revolutionized our world, right from paying bills to enjoying shopping online. Apparently, we are experiencing the influence of innovative technology in everyday life. But, as far as these impulsive trends are shifting towards fierce technology, we are more at the stake of security threats.
A recent threat of 360 million stolen credit card accounts (which were up for sale in cyber black market) have encountered by a cyber security firm. This is not the only threat; there are a number of attacks that have been previously detected and undoubtedly coming next to us. So, it is imperative to maintain utmost security in order to ensure that your confidential customer details remain secure. Moreover, it will also help you save millions of dollars that may incur on you owing to consumer lawsuits.
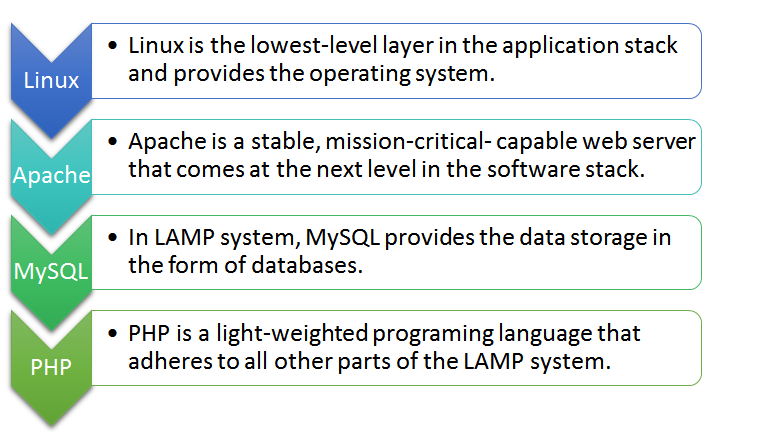
In this blog post, I have accumulated certain facts that will help you keep your LAMP based servers at bay from vulnerabilities. LAMP is one of the most popularly used web development framework, consisting of the four components, i.e. Linux, Apache, My SQL, and PHP that are structured in a layered way. Each layer supports a critical part of the entire software stack.
Shielding Your Servers Against Nefarious Attacks
For this very reason, it is inevitable that your Apache web server is perfectly configured, maintained and monitored, so that it is not exposed to vulnerabilities.
In this blog, you can see both general guidelines that you can follow to secure your dedicated server hosting, and the important steps that you should consider in order to mitigate the damage caused by such attacks.
Steps to be Followed in Securing Your Web Server
For Servers with Apache
- Hide the Apache version number and other sensitive information by following the steps listed below:
Add or Edit the following two directives, which exists in httpd.conf file
Server Signature off
Server Tokens Prod
The server signature appears on the bottom of pages generated by Apache web server such as 404 pages, directory listings, etc.
Server Tokens Prod directive is basically used to determine What Apache will put in the Server HTTP response header.
- Make sure your Apache version is running under its own user account and group. It is the optimal way to add a separate user “Apache” and then modify the given directive in httpd.conf to run apache as its own user.
User apache
Group apache
- Make sure that files outside the web root directory should not be accessible to any of the users.
<Directory />
Order Deny,Allow
Deny from all
Options None
AllowOverride None
</Directory>
<Directory /html>
Order Allow,Deny
Allow from all
</Directory>
Note: As we set “Options None” and “AllowOverride” None in the above code, it will turn off all the options and overrides for the server only. Now, you can explicitly add them for each directory that requires an Option or Override.
- Turn off the directory browsing, and then follow symbolic links and CGI execution. You can perform this through an Options directive inside a Directory tag.
Turn off all the options by simply using
Options None
In spite of that, if you want to turn off a very few, separate each option with a space in your Options directive:
Options -ExecCGI -FollowSymLinks –Indexes
- Install modsecurity
Modsecurity is an Apache add on module, through which you can detect and prevent http attacks. It is the best way to prevent SQL injections in case your web developer forgets to add input validation. Information can also be breached if developers fail to identify and block information disclosure issues such as leaking detailed error messages, Social Security Numbers or Credit Card Numbers
Follow these methods to install mod-security
On CentOS:
yum install mod_security
On Ubuntu:
apt-get install mod_security.
service httpd restart
- Disable all unwanted modules that are enabled on your Apache Web Server.
To search for installed modules, you can run following command:
grep LoadModule httpd.conf
Here is the list of some modules that are typically enabled and you don’t even need them.
mod_imap
mod_include
mod_info
mod_userdir
mod_status
mod_cgi
mod_autoindex.
To disable them, add a # sign in front of each module
- Lower the Timeout value which is by default set to 300 seconds. Decreasing this value helps in reducing the potential impacts of a denial of service attack.
Timeout 45
-
Restrict large requests
To mitigate the effects of a denial of service attack, restrict the amount of body that can be sent in an http request. If you don’t need large uploads, then you can limit this to 1MB via following directive.
LimitRequestBody 1048576
9. Application and Database Security is essential to prevent SQL injection from extracting data from poorly coded websites. Here is how you can prevent it.
- Make sure that your web applications like Joomla, WordPress, and Drupal are upto date.
- Subscribe to Bug updates and Vulnerability reports.
- Avoid word writable 777 permissions to your files or folders.
- On regular basis, check for viruses or infections by scanning your web package.
- If you are using MySQL or MariaDB, run the MySQL secure installation script.
- If your application requires you to store sensitive information like username, passwords, credit card data etc. then ensure that all communication is encrypted by using a Digital Certificate method.
For servers with PHP
1. Run PHP as a separate user rather than as an Apache module. If you install php as an Apache module, the php script run as per the Apche user permission and it becomes more prone to the security vulnerable attacks.
A good option to install php would be with php-fpm a fastcgi process manager which enables you to run and manage php scripts as a separate user.
- Always make use of POST method to pass important parameters like usernames, passwords, credit card information, etc.
- Always validate Form and Text Input, because there is a risk of cross site scripting that allows hacker to run malicious code on your server by simply uploading a file with malicious code in it.
- Hide the PHP version through php.ini file and add the following
Vim /etc/php.ini
expose_php = Off
- Log all php errors to a file and not on the website
display_errors = Off
log_errors = On
error_log = /var/log/httpd/php_error.log
For dedicated or VPS Hosting with MySQL or MariaDB
- Run MySQL Secure Install
After installing MySQL run the mysql_secure_installation script
sudo /usr/bin/mysql_secure_installation
This code will prompt you to add a MySQL root password, lock root access to localhost and remove any unwanted databases like the test database.
- Secure MySQL by logging into your MySQL server and make sure that all MySQL users have a password. Further, delete unnecessary user, if any. Grant access to only authorized users.
All the steps and procedure mentioned above helps in ensuring that your customer’s data remains secure and away from all nefarious acts.






 Live Chat
Live Chat

I don’t feel secured shopping online and keeping my valuable information on my mobile device. That’s e prefer going to the store and buy what i want and i never connect on public wifi for my protection. Much more on the business, its more vulnerable to cyber attacks.
Way cool! Some very valid points! I appreciate you penning this post and the rest of the website is extremely good.
Simply want to say your article is as astonishing. The clarity in your post is just nice and i can assume you are knowledgeable in this subject. Fine with your permission allow me to seize your RSS feed to stay updated with drawing close post. Thanks one million and please keep up the rewarding work.
If you would like to grow your familiarity just keep visiting this web site and be updated with the most up-to-date news update posted here.
Wow! After all I got a web site from where I be able
to in fact obtain helpful data regarding my study and knowledge.
I’m really enjoying the design and layout of your blog.
It’s a very easy on the eyes which makes it much more pleasant for me to come here and visit more often. Did you hire out a developer to create your theme? Superb work!
Excellent site you’ve got here.. It’s hard to find high quality writing like yours these days. I truly appreciate people like you! Take care!!