There are millions of cyber attacks being inflicted on websites that may suffer heavily casualties in absence of rock solid defense measures. Hackers have gained advanced capabilities, thanks to easy availability of automated hacking tools. Wireless Application Firewall deserves a significant position among all technologies that are aimed at prevention of web based attacks that may originate from familiar or unidentified sources of application threats.
Emergence of WAF
Traditionally, firewalls have proved to offer effective defense against intruders with criminal intentions and it is but natural that these have undergone evolution to match growing threats that are being executed with advanced skills and amazing speeds.
The real risk presented by threats that could not be thwarted by legacy firewalls was their potential to impact the application itself as these threats executed attacks by using HTTP and other authorized protocols. These attackers could gain direct access to systems for hacking sensitive data.
Web Application Firewalls came into existence to effectively arrest modern cyber threats as the traditional firewalls could not offer reliable protection. There are several iterations of WAFs in relation with the extent of benefits that are offered for different costs.
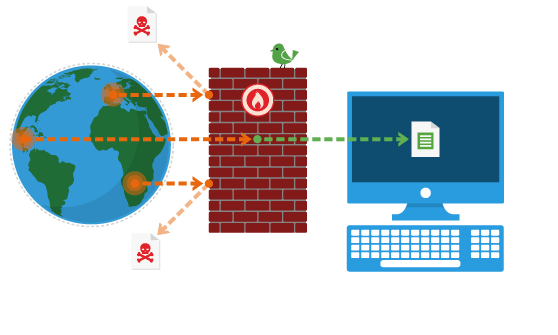
Different methods of implementation
The most basic implementation of a Web Application Firewall is known as network based WAF, which is essentially a hardware intensive firewall technology. Another feature of a network oriented WAF is its local implementation and the two features can be attributed to its advantages as well as disadvantages. Users can achieve remarkable latency mitigation due to its local characteristics in addition to reduction of impacts due to negative performance. Major drawback of network based WAF is the high upfront costs as well as expensive operation and maintenance.
Networking team is usually assigned with responsibility to look after management of network based Web Application Firewalls. Reputed vendors help users implement large scale configuration or deployment by replicating settings as well as rules. Centralized configurations and signatures further simplify process of securing multiple applications with considerably less efforts and expenditure.
Web Application Firewalls can be integrated fully within the application code or installed on the hosting platform to create an application based WAF for enhanced customizability as well as improved performance. This type of WAF is also much more economical due to lack of any hardware equipment. The most significant demerit of the application based WAF is its relative lack of scalability in large organizational setup.
Since application based WAFs reside locally, their management can be overwhelming as these WAFs are designed to integrate into applications. This implies necessity of local libraries apart from seamless access to multiple local resources such as compute power, RAM, and disk space within environment that is compatible. You should also note that these WAFs are built entirely as software programs, which requires active participation of security as well as server management teams throughout the process of installation and future management.
You will have to deploy cloud based Web Application Firewalls with hundred percent support of a cloud hosting service provider who will also look into the management aspects of these firewalls. Customers are required to involve their management and security team for its configuration by providing access to cloud based WAFs via web interface. These teams will be allowed to tweak the settings to define response of WAF in terms of different cyber threats. The threats may cover some of the most dangerous attacks including SQL injection and also the most dreaded DDoS attack. Needless to mention, your security and management team will also be empowered to switch off specific rule sets as per the need of the hour.
Amazing features of WAFs
Having understood various types of Web Application Firewalls we can now focus on some of the most interesting attributes of these modern security tools. If you are thinking that the advanced WAFs are only capable of blocking unwelcome or potentially dangerous traffic, then you are mistaken. The filter tool of some of the advanced WAFs is capable of not only preventing entry to the bad visitors but these firewalls can also attract good visitors to your site.
Firewall filters act as noise suppressors to improve site’s visibility for better ranking by websites. This is further backed by use of Content Delivery Network to facilitate potential as well as good visitors to find and visit your site without much difficulty. Combination of CDN and WAF is found to be a synergistic one and it enables qualified customers to drop in and browse your web presence for a greater monetization.
Web Application Firewalls are equally accountable for thwarting the bad guys from reaching your site so that your web presence grows without concerns of cyber threats. There are multiple service providers to choose from if you are interested in empowering your site with a hardened security profile that has ability to attract good traffic.






 Live Chat
Live Chat