Prevention of data Protection intrusion attempts that result in data leaks is the most vital objective of any organization’s security strategy. According to some reliable studies, eight out of ten hackers can break into a system within less than sixty seconds. This sounds extremely uncomfortable because a cyber attack is similar to cancer that spreads to cover the entire system.
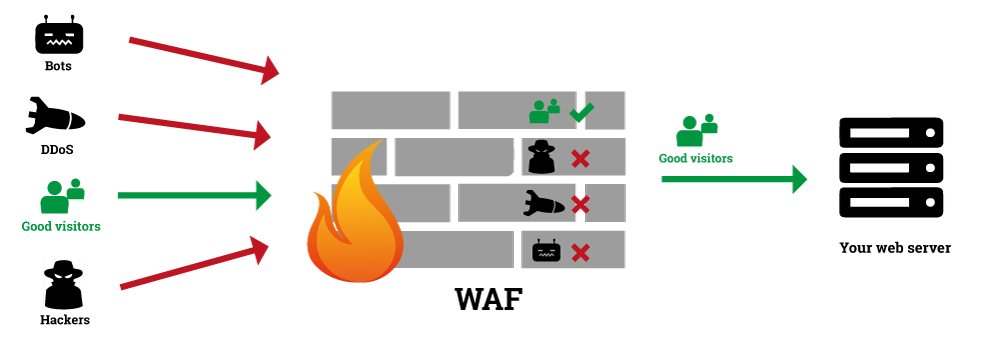
Web Application Firewall is a modern avatar of traditional firewall measures adopted by security conscious enterprises. It is necessary to upgrade legacy firewall tools because the modern hackers are in possession of technologically advanced hacking tools that can penetrate traditional measures to prevent intrusion.
Extent of knowledge about data
Familiarity with various aspects of organizational data is a primary need to develop consciousness about security of the digital assets of an organization. One must have an in-depth knowledge about company’s data in terms of different levels of security requirements as a sensitive data will need to be backed by tougher security measures and so forth. Similarly, location of data also plays vital role since there are multiple locations that could be assigned with job of data storage. These locations are network terminals, servers, and storage disks to name a few.
 Locations of data storage must be classified on the basis of security needs of the stored data because if you are dealing with highly sensitive user login credentials such as passwords, account information, and even personal health information, then such data will carry the highest risk of being attacked. Naturally, your entire focus will have to be on this type of data while creating security infrastructures.
Locations of data storage must be classified on the basis of security needs of the stored data because if you are dealing with highly sensitive user login credentials such as passwords, account information, and even personal health information, then such data will carry the highest risk of being attacked. Naturally, your entire focus will have to be on this type of data while creating security infrastructures.
Knowledge about data in terms of sensitivity and locations comes handy at the time of assigning roles, permissions, and fixing vulnerabilities in a given system. Concerned staff must be careful while managing locations of critically important data and should frequently upgrade server infrastructures for enhanced security of mission critical data.
Possible risk potential of permissions
There have been several instances of crimes related to industrial spying because some personnel are prepared to steal ad sell classified information for monetary benefits. Unless you have assigned permissions to right individuals, your sensitive data will be always exposed to wrong individuals who may secretly share it with outsiders.
Assigning permissions and responsibilities to trusted employees can be a logical approach. This can also include multi-factor-authentication, frequent password changes, and regular security audit. You can also disable internet access and use of thumb drives in case of general population of employees so that data theft can be prevented. Modern organizations are found to train their staff as far as security awareness is concerned.
Importance of data encryption
The most vital phase that makes data highly vulnerable to intrusion by cyber criminals is the transmission phase. Similarly, your data can also be hacked easily while it is being generated especially if the same is not protected by way of data encryption. Hackers can adopt a wide array of attacks including phishing, DDoS attack, intruding, or hijacking to get hold on the sensitive information.
Data leak can jeopardize your business operations or hacker’s demand for a ransom can shatter you financially. Https and App Transport Security are some of the most commonly implemented security standards. It is recommended to provide a secure environment in order to protect data at every stage including its generation, transmission, and reception.
Knowledge about industry specific attacks can be very important for anticipating the type of threats to gain immunity against these. In addition to this, one must be prepared to deal with a large spectrum of web attacks that could be in the form of SQL injection, credential stuffing, and phishing among others.
There is no use of deploying a long list of security products because security requirements of every enterprise are not similar. This calls for a tailor-made strategy for selection of specific security products. You may leverage services of security consultants to understand nature and type of threats in terms of events and risks that would be most probably encountered by your site.
Timely intervention
Postponement of addressing vulnerabilities that are identified as serious threats can be extremely dangerous and a large population of websites are found to put off important security decisions. Such delays can result in serious consequences. Every security minded organization must have systems in place that consistently deliver vulnerability scans in addition to seamless monitoring of applications with timely patching and upgrading.
Sometimes, vulnerability could be of serious nature as far as safety of important data is concerned unless one takes action immediately. This calls for a no compromise attitude while dealing with vulnerabilities and these must be identified and fixed instantly or as soon as possible.
In conclusion
Web Application Firewall guarantees assured defense against a broad array of cyber attacks. Alibaba Cloud has been developed as an ideal security tool for large organizations and commerce portals.






 Live Chat
Live Chat
Hi there! This is kind of off topic but I need some advice from an established blog.
Is it very difficult to set up your own blog?
I’m not very techincal but I can figure things out pretty quick.
I’m thinking about setting up my own but I’m not sure where to begin.
Do you have any ideas or suggestions? Many thanks