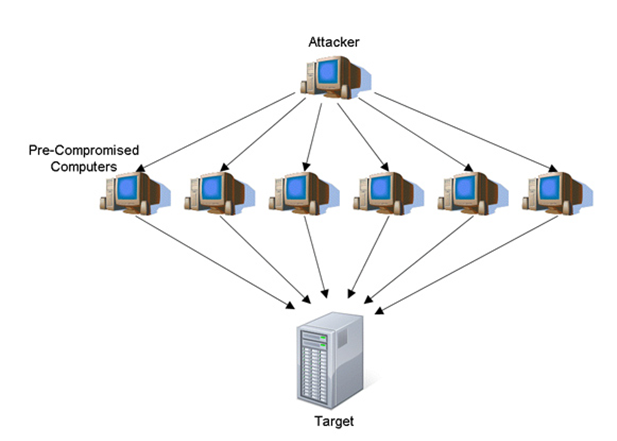
Scams, whether the ones that surface in the national and international polity or in the cyber world – do not seem coming to an end. Forward-thinking business leaders try to revamp their security roadmap to protect the confidentiality, integrity, and network availability for their procedures. Until the recent times, the investments were more focused on protecting the integrity and confidentiality, not the network availability. Many studies vociferate changing the approach related to the network security, keeping in view the fact that the Distributed Denial of Service (DDoS) attacks on network have relatively become rampant, crippling the abilities to perform legitimate business operations. It sends an enormous amount of fake traffic to a given server, overwhelming it and taking it down.
DDoS is a spiteful technique that slams targeted servers with numerous numbers of bot-created requests having an aim to wreck the legitimate business functionalities. These pernicious techniques, nowadays, are the most prevailing and costly part of cybercrime. When DDoS attacks the sites, like WordPress, it casts serious repercussions. If reports are to be believed, this ubiquitous tool of hackers is targeting mission-critical websites, smacking down even the biggies in market. Some of the known reasons of these attacks are subjected to extortion, prejudice, revenge, or gaining a competitive edge. Businesses are constantly on the lookout for techniques that can help them protect their data center architecture, without over-spending on security modules. Well, the good news is DDoS attacks can be defended strongly.
The foremost step is to determine the average cost of service outages. Second, comprehend the probability of attacks on your organization and encounter outages. Once evaluated, apply a risk management strategy keeping in mind the time, size, cost, risk, and effectiveness of such attacks.
Here are a few the techniques that can help you protect your website:
Use Virtual Private Networks over Public Networks: A Virtual Private Network (VPN) is created using a virtual point-to-point connection with the help of dedicated connections, traffic encryption, or virtual tunnelling protocols. It helps in connecting your mission-critical website to a secure, offsite server. Above all, high-end encryption technology is used to protect your confidential data and transactions against a host of attacks. It protects your website from the hackers, tracking your online activities through public networks. VPN emerges as a bountiful solution to curtail such kind of attacks on the network. Another smart feature linked with VPN is anonymity, which enables you to access any restricted websites (which are blocked owing to regional factors). Well, as the prime target of DDoS attackers is to seek your IP address. The question that originates here is, if you can access the IP address of a particular website to bombard the illegitimate requests to your server. As VPN enables you to keep your identity hidden, attackers will not be able to discover it.
Plugins: Well, for the websites built on WordPress have good news. You must be aware of the fact that WordPress offers hundreds of plugins that can extend the functionality of a website. There are plugins that can protect your business against DDoS attacks, provided if implemented effectively.
Note – Undeniably these tools are effective, however it is important to extend your security shells by closely monitoring your website. If any fluctuation you discover, take immediate actions to fix.
ISP: A few of the organizations make use of their ISP to curtail DDoS attacks. When compared to an enterprise’s own bandwidth capacity, these Internet Service Providers have more bandwidth, which can further help with the large volumetric attacks. However, it has some flaws as well, like – dearth of competency, and protection.
Cloud Mitigation Provider: Today, there is a plethora of cloud mitigation providers offering Distributed Denial of Attack services from the cloud. To put it simply, these forward-looking vendors have built our extensive amount network capacity and DDoS mitigation capacity at different sites across the Internet that has the potential to cope up with the exceeding user requests – no matter whether your business is utilizing multiple ISP’s , own data center, or a cloud hosting vendor. This, in turn, ensures that only legitimate traffic reaches to your website. Think – when only clean traffic reaches to your website –there are negligible chances for attackers to succeed in their bad intentions.
Choosing a cloud mitigation provider can be a bountiful bet as they have the right techniques, multitude of DDoS mitigation hardware equipment, and pool of network resources to cater to the different DDoS protection needs. Above all, they have the expertise to provide you quick assistance to deal with the same.
Partner with a Reliable Hosting Vendor: Half of your website success and reputation depends on the hosting vendor you have picked to partner with. A well-positioned data center service provider will have all the necessary equipment including firewall, and vulnerability scanners to mitigate DDoS attacks.
These specialized vendors have a team of network and security engineers who closely monitors switches and routers so that your business runs uninterruptedly. The best part is they have state-of-the-art data center infrastructure that can accommodate sudden peaks in demand without causing any downtime issues.
DDoS is a troubling notion. It goes without saying that commoditization of these malevolent attempts has left many websites vulnerable. Moreover, the pace at which Internet of Things (IoT) is growing, more opportunities for attackers will evolve to leverage devices to multiply the size and scope of their botnets. It is important that data center providers should include a proactive strategy for incorporating DDoS protection into their security and disaster recovery planning. Select a vendor that incorporates DDoS protection modules, power-packed firewall protection with robust DDoS defense features, and employs cloud hosting based scrubbing services to endure such kinds of attacks.






 Live Chat
Live Chat


After exploring a number of the articles on your website, I honestly like your technique of blogging. I bookmarked it to my bookmark web-page list and will be checking back soon. Take a look at my web site as well and let me know how you feel.