Linux servers are poised to considerably revitalize the way software applications are built, deployed, and instantiated. Designed to respond to the changing market demands including database management, proliferating web services and network system administration – these severs are high-potential variant of Linux open source operating system that includes CentOS, Slackware, Debian, Ubuntu Server, and Gentoo.
Linux Server: A Buzzing & the Most Demanding Data Center Asset
 Being the most preferential operating system alternative over other pre-existing applications – Linux has protracted its range to a staggering level, transversely all industry verticals. Fundamentally, Linux loaded servers frequently setup a connection with clients operating on other operating system variants, such as Microsoft Windows. These servers are responsible for serving files created on and for such platforms.
Being the most preferential operating system alternative over other pre-existing applications – Linux has protracted its range to a staggering level, transversely all industry verticals. Fundamentally, Linux loaded servers frequently setup a connection with clients operating on other operating system variants, such as Microsoft Windows. These servers are responsible for serving files created on and for such platforms.
Now, let’s take a sneak peek of the factors that makes Linux a demanding data center constituent:
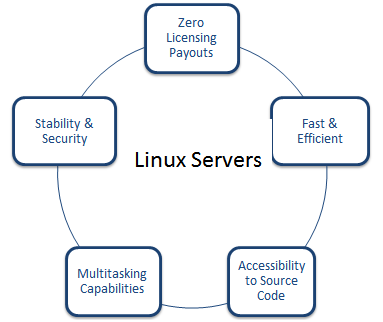 Questions must be cropping up in my reader’s mind that if it is so effective than how nefarious acts can intrude and affect its functionality. Right? To be precise, Linux servers are incontestably a perfect match to meet the demands of ‘bit turning to zettabyte’ business realm. Here is the catch, these servers function in an optimal way – provided if they are controlled, managed, and loaded with requisite security applications and monitored pertinently. Right from sharing files to Facebook or Wall Street serving real-time data to multiple concurrent end-users – Linux is the prime choice for everyone. Although Linux includes security mechanism like SELINUX, but sometimes even a small bug can give way to hackers, making it difficult for your business to sustain in the market.
Questions must be cropping up in my reader’s mind that if it is so effective than how nefarious acts can intrude and affect its functionality. Right? To be precise, Linux servers are incontestably a perfect match to meet the demands of ‘bit turning to zettabyte’ business realm. Here is the catch, these servers function in an optimal way – provided if they are controlled, managed, and loaded with requisite security applications and monitored pertinently. Right from sharing files to Facebook or Wall Street serving real-time data to multiple concurrent end-users – Linux is the prime choice for everyone. Although Linux includes security mechanism like SELINUX, but sometimes even a small bug can give way to hackers, making it difficult for your business to sustain in the market.
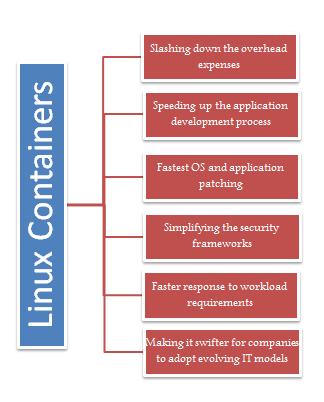
Getting into Technicalities: A Driving Force behind Major Linux Adoption
Briefly, a Linux server can be isolated into several containers using hypervisors that provides a logical abstraction at the hardware level. Here each container runs in isolation and shares an operating system instance. Point that I want to emphasize on here is that a container can encapsulate any application dependency. Let’s say that, if a website runs on a specific version of the ASP.net, the Linux container can easily encapsulate that version, which in turn allow multiple versions of the same scripting language to be there in the same environment, and that too without bearing administrative overhead of a complete software stack, including the OS kernel.
Through this blog, I attempt to make my readers aware of some of the conquering tips and trials that can help them keep their servers at bay against annihilating factors:
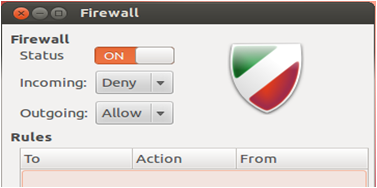
Firewalls: Firewalls are one of the significant parts of any server configuration, helping businesses to protect their critical data and applications from unwarranted access. It restricts access depending on the categories, namely public, private, and internal services. In technical depth, it is a software application that restricts network traffic and access to insecure websites. There are a host of open source firewalls available for download such as Iptables, IPCop, Shorewall, UFW, Vuurmuur, pfSense, and so on. Also, Linux comes with built-in firewall that allows users to tune and configure the rules, based on the operational and organizational needs.
Secured Passwords: Passwords are important to shield your critical data assets against forced access. Try implementing strong and unique passwords for each of your accounts. Remember, don’t use the same password for all; it’s a worst practice that can break your business wheels. A weak or common password can give access to your foes into your computer.
Tricks: You can use paraphrases, formulas, and spaces to make your password more strong and unforgettable. Also you can make use of password managers for the creating and remembering secure passwords.
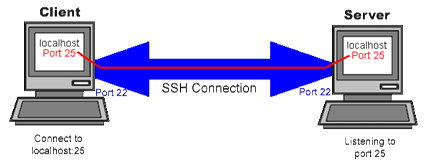
SSH Keys
Secure Shell (SSH) is a network protocol that helps in establishing secure data transmission between two network devices. The encryption technology integrated in SSH protects confidential and integrity of information over non-reliable network, such as Internet. In this, public cryptography is used to substantiate the remote computer and thereafter enables that particular computer to authenticate the user. Encryption is the best technique to hem in your data into secured walls.
Virus Scanners: Viruses can shake your business’s bottom line by interfering or sometimes stealing your confidential data and sending across to wrong hands. Keep your servers 1000 miles away from infectious elements. Install a robust virus checker on your Linux server and keep on scanning it after few days or weeks. Also, keep your system updated with all the requisite security applications. On top of it, ClamAV is one of the best-in-class open source virus checking program that comes with Linux. It includes multi-layered scanner daemon and supports a host of file formats including signature languages.
Enable WPA on your router
Wireless connection is an indubitable aspect to access and transfer the content online. However, as long as the data is transmitted over the network, you have the probable chance of compromising to security. To add rigorous security in your wireless connection, it is imperative to enable encryption tools so that no one can open a nasty hole to your router. Among the standard security methods, some widely popular methods are WEP (Wired Equivalent Privacy), WPA (Wireless Protected Access), and WPA2. Using some encryption tools is always a secured choice than using none. However, WEP is the least secure of these standards, implies that it can be easily compromised. That’s why it is better to enable WPA (Wireless Protected Access), which ensures safety in your local area network. On top of it, the second version named as WPA2 is the most secure encryption tool that scrambles the network connection, ensuring that no one keeps an eye on what you are accessing.
WPA key takeaways include:
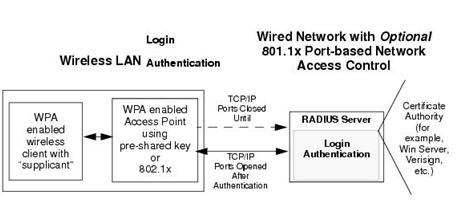
WPA Authentication Process: Enterprise-level User Authentication via 802.1x/EAP and RADIUS
WPA eliminates most of the known WEP vulnerabilities, which is primarily envisioned for wireless infrastructure networks. This infrastructure involves stations, access points and authentication servers known as Remote Authentication Dial-In User Service servers (RADIUS servers). RADIUS server holds user credentials to authenticate wireless users before they gain access to the wireless network. WPA incorporates an integrated sequence of operations such as 802.1X/EAP authentication and sophisticated key management and encryption techniques to add security.
The Bottom Line: Today end-user demands from technology is plunging a step forward rampantly, demanding full-fledged IT solutions that include fastest deployment, patching, monitoring, and configuration in order to meet varying business and IT requirements. However, it is essential to ensure that what kind of service entitlements including security businesses wish their systems to have prior hemming in into the service bonds.






 Live Chat
Live Chat




Thanks admin for sharing this information, it is worth to read.